Zero Trust Architecture has become one of the most widely discussed cybersecurity frameworks today because it is built on a fundamental principle, assume nothing is safe and protect everything.
After post-pandemic digital expansion, enterprises operate across hybrid cloud environments, remote networks, SaaS applications, and mobile devices. As a result, legacy perimeter-based security models have become obsolete.
The very concept of trust within the network is now a vulnerability. Zero Trust introduces a paradigm shift by eliminating implicit trust and enforcing continuous verification for every user, device, and connection.
In this blog, we will explore what Zero Trust Architecture is, why traditional models fail, how Zero Trust operates, and how it strengthens their cybersecurity posture.
Understanding Zero Trust Architecture
Zero Trust Architecture is not a single technology but rather a strategic framework that treats every access request as potentially hostile, regardless of its origin.
Unlike traditional perimeter-based security models that operate like a castle-and-moat approach, Zero Trust eliminates the concept of a trusted internal network entirely. Every user, device, and application must prove its identity and authorization continuously, with trust never being a static, one-time event.
Key Components of Zero Trust Architecture
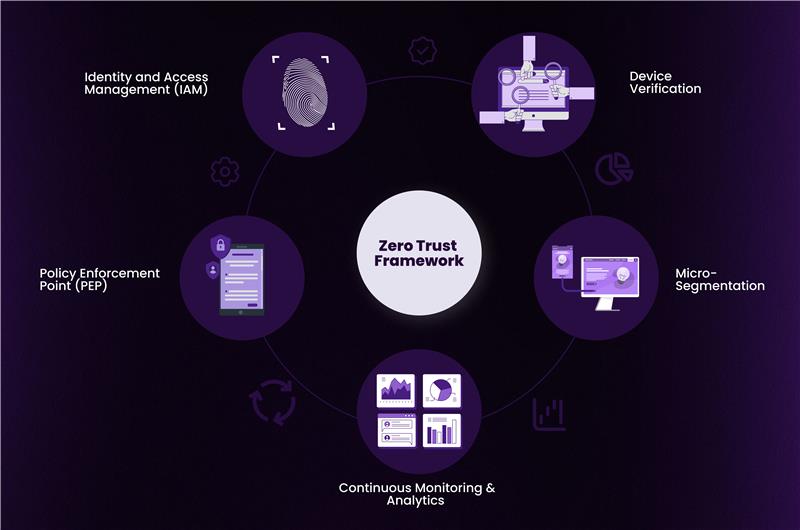
Zero Trust is an integrated approach that brings together multiple security capabilities:
1. Identity and Access Management (IAM)
This is the heart of Zero Trust. Every interaction must be verified.
- Multi-factor authentication (MFA)
- Single sign-on (SSO)
- Passwordless authentication
- Role-based and attribute-based access control (RBAC/ABAC)
IAM ensures that only legitimate, authorized identities gain entry.
Every device that connects to your network must be validated.
2. Device Verification
- Endpoint Detection & Response (EDR)
- Device compliance checks
- Mobile Device Management (MDM)
3. Micro-Segmentation
Instead of a flat internal network where everything is connected, Zero Trust breaks the network into isolated segments. If an attacker compromises one segment, they can’t automatically access the rest.
Think of it as having multiple vaults inside a bank, each requiring separate authorization keys.
4. Continuous Monitoring & Analytics
Zero Trust is not “set it and forget it.” It requires real-time visibility into traffic, user behavior, and access logs.
- AI-driven anomaly detection
- Real-time threat intelligence
- Security Information & Event Management (SIEM)
5. Policy Enforcement Point (PEP)
All access requests flow through policy engines that evaluate whether access should be granted based on dynamic conditions.
- User identity
- Device health posture
- Time and geographic location
- Behavioral analytics
Zero Trust vs. Traditional Perimeter Security
Traditional perimeter-based security operates on the “trust but verify once” model. Once a user enters the network, they gain broad access to resources. As of now, 63% of organizations globally have fully or partially implemented zero-trust strategies, and 97% of companies either adopting or planning zero-trust initiatives.
This approach assumes that internal networks are secure environments, an assumption no longer valid in the age of cloud computing and remote work.
Key Drawbacks of Legacy Models:
- Perimeters are ineffective against insider threats and credential theft.
- Cloud services and remote access bypass traditional perimeter defenses.
- Threat detection is slow and reactive rather than proactive.
According to industry reports, a large percentage of breaches involve internal actors or compromised credentials rather than external hacking alone. Zero Trust addresses these vulnerabilities by removing implicit trust altogether.
Benefits of Zero Trust Architecture
1. Minimized Attack Surface
Zero Trust restricts access strictly to what is necessary.
Users, devices, and applications are never assumed to be trustworthy simply because they are inside the network.
By enforcing least-privilege access and continuously validating every request, Zero Trust significantly reduces opportunities for attackers to exploit vulnerabilities. Network visibility is also limited, making it difficult for unauthorized actors to identify and target critical assets.
2. Improved Breach Containment
In traditional architectures, once a threat actor breaches the perimeter, they can often move freely through internal systems. Zero Trust stops this lateral movement through micro-segmentation and continuous authorization.
Even if one segment is compromised, the threat is contained and isolated, preventing it from spreading to mission-critical systems or sensitive data.
3. Enhanced Visibility and Control
Zero Trust centralizes visibility across users, devices, workloads, and data flows. Every access request is logged and evaluated in real time, providing deep operational insight.
This unified view enables faster detection of anomalies and empowers security teams to respond to potential threats before they cause disruption.
4. Regulatory and Governance Alignment
Zero Trust aligns with modern compliance requirements by enforcing strong identity controls, data segmentation, and continuous monitoring.
It builds an auditable framework that supports data protection laws and industry regulations, helping organizations meet compliance mandates more efficiently while reducing legal and reputational risk.
Conclusion
Zero Trust Architecture is rapidly becoming a foundational requirement for enterprise cybersecurity. As digital ecosystems expand across cloud environments, remote operations, and interconnected supply chains, the traditional perimeter-based approach is inadequate against modern threats.
By assuming that no user, device, or application should be inherently trusted, organizations can significantly reduce cyber risk, contain potential breaches, and gain full visibility into their digital landscape.
More importantly, Zero Trust enables long-term security maturity, operational continuity, and regulatory readiness.
If you’re looking to create content tailored to your ideal customer profile that also ranks well on search engines, get in touch with us.





